Services / SOC
Security Operations Center
consulting
consulting
We have created a comprehensive Security Operations Center (SOC)
framework to help you keep your SOC up with the time
framework to help you keep your SOC up with the time
How does it work?
Our Framework
Maintain your defenses against evolving digital threats. Each aspect of our SOC support is designed to fortify your organization’s resilience against cyber incidents:
KPI Analysis & Reporting
Measure and report key performance to drive security improvements.
Threat Intelligence
Gather and analyze data on emerging threats to stay ahead.
Security Orchestration, Automation and Response
Integrate systems and automate responses for efficiency.
Threat Hunting
Proactively search for and mitigate potential threats.
SIEM Log Monitoring
Monitor and analyze security event logs for signs of incidents.
Network Intrusion Detection & Prevention
Detect and block unauthorized access attempts.
Endpoint Security
Secure user devices to prevent entry points for threats.
Vulnerability Assessment & Penetration Testing
Identify and test system weaknesses to strengthen security.
Incident Response
Respond to and recover from security incidents effectively.
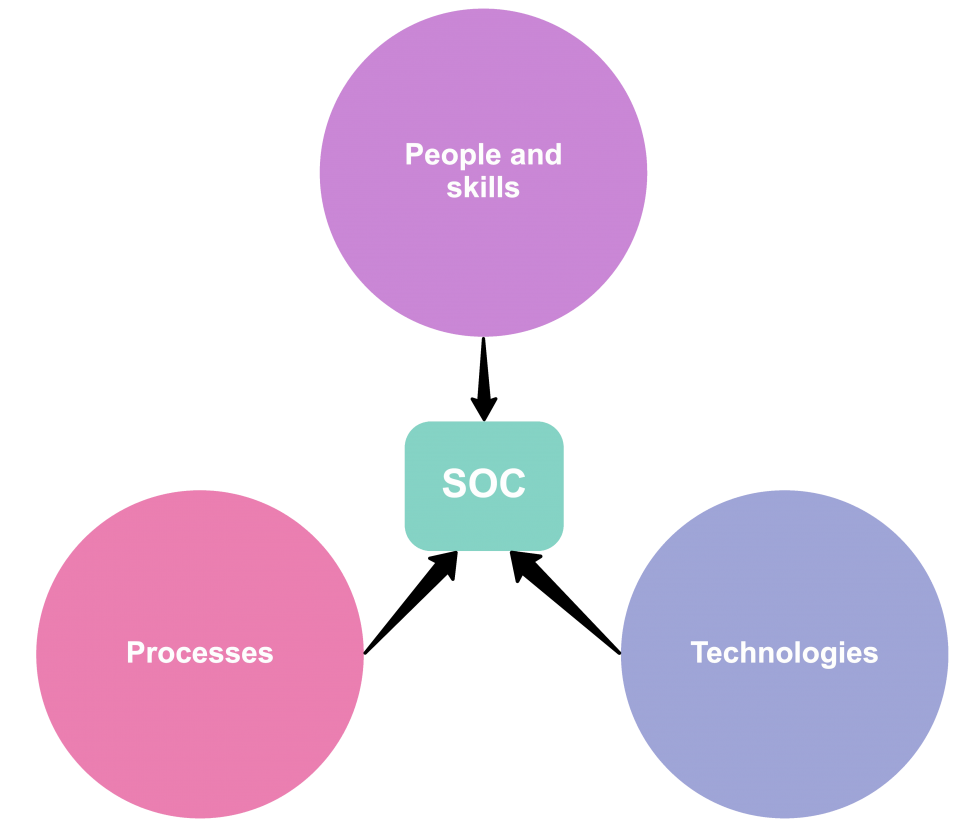
Let us transform your SOC by:
Implementing the necessary SOC Tools and Technologies
Defining clear processes and standards
Filling the roles with skilled employees and ensure continuous training
Technologies
SOC’s success depends on collection of the right data, correlation, detection, analysis and management technologies:
Security Information Event Management (SIEM)
Vulnerability scanner
Network Intrusion Detection and Prevention
Threat Hunting
Threat intelligence
Security Orchestration, Automation and Response (SOAR)
KPI Analysis and Reporting
Processes
To ensure continuous quality alerting, key processes should be defined a SOC analyst follows (eg. in form of checklists or playbooks) to ensure no important tasks fall through the cracks.
Event classification & Triage
Prioritisation, Analysis & Escalation
Remediation & Recovery
Assessment & Review
Reporting & Documentation
Build Knowledge base and ensuring
People and skills
The best tools, technologies and processes will not be effective without skilled staff. Continuous formal, vendor-specific and internal trainings are key!
Roles and responsibilities:
Tier 1: Alert Analyst
Tier 2: Incident Responder
Tier 3: Subject Matter Experts (SME)
Tier 4: SOC Manager
SOC Head
Our Partners











